2. Overview
2.1 High‑level architecture
-
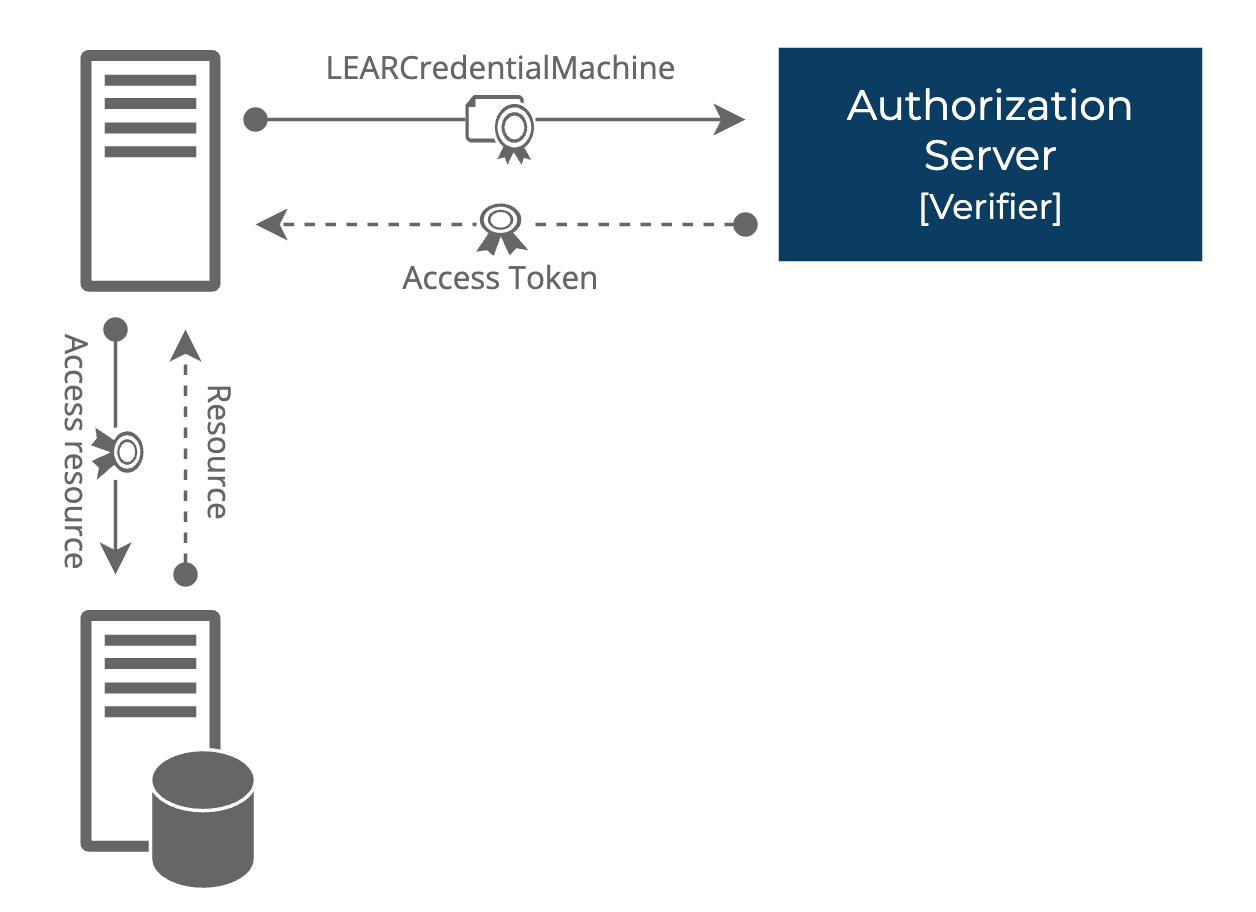
Client requests access token from Verifier Token Endpoint using client_credentials grant and client_assertion = VP (containing LEARCredentialMachine).
-
Verifier authenticates client, validates VP and LEARCredentialMachine.
-
Verifier issues access token with 1h lifetime.
-
Client uses access token to call protected resources.
2.2 High-level flow
-
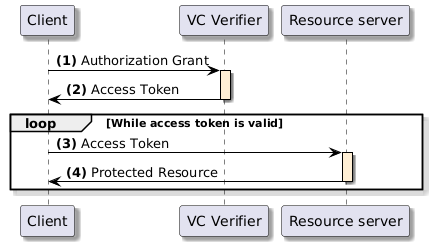
The client requests an access token by authenticating with the authorization server (VCVerifier) and presenting the authorization grant. Since the client authentication is used as the authorization grant, no previous authorization request is needed.
-
The authorization server authenticates the client and validates the authorization grant, and if valid, issues an access token.
-
The client requests the protected resource from the resource server and authenticates by presenting the access token.
-
The resource server validates the access token presented and if valid, returns the resource requested.